
Hackers are concentrating on older variations of the HTTP File Server (HFS) from Rejetto to drop malware and cryptocurrency mining software program.
Risk researchers at safety firm AhnLab imagine that the risk actors are exploiting CVE-2024-23692, a critical-severity safety challenge that enables executing arbitrary instructions with out the necessity to authenticate.
The vulnerability impacts variations of the software program as much as and together with 2.3m. In a message on their web site, Rejetto warns customers that variations 2.3m by way of 2.4 are “harmful and shouldn’t be used anymore” due to a bug that lets attackers “management your laptop,” and a repair has but to be discovered.
Supply: ASEC
Noticed assaults
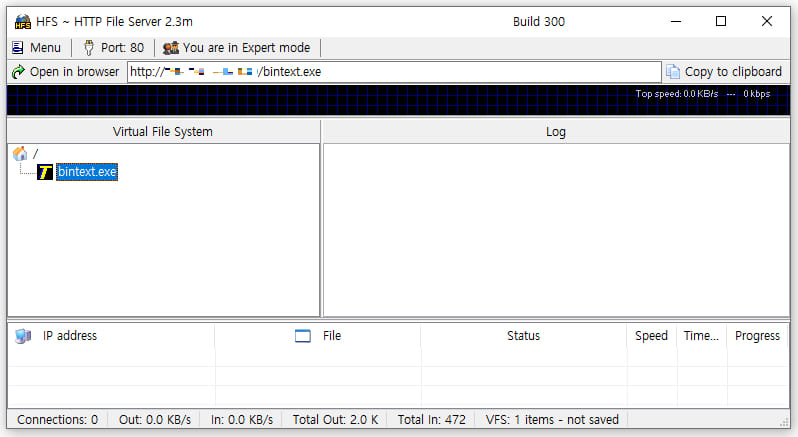
AhnLab SEcurity Intelligence Middle (ASEC) noticed assaults on model 2.3m of HFS, which continues to be extremely popular amongst particular person customers, small groups, academic establishments, and builders that wish to check file sharing over a community.
Due to the focused software program model, the researchers imagine that attackers are exploiting CVE-2024-23692, a vulnerability found by safety researcher Arseniy Sharoglazov final August and disclosed publicly in a technical report in Could this 12 months.
CVE-2024-23692 is a template injection vulnerability that enables unauthenticated distant attackers to ship a specifically crafted HTTP request to execute arbitrary instructions on the affected system.
Quickly after the disclosure, a Metasploit module and proof of idea exploits turned accessible. In response to ASEC, that is across the time exploitation within the wild began.
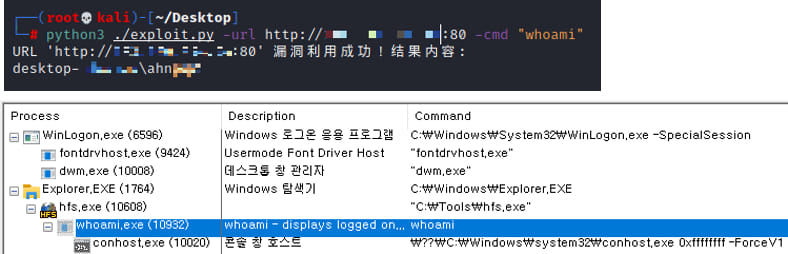
The researchers say that throughout the assaults the hackers accumulate details about the system, set up backdoors and numerous different sorts of malware.
Attackers execute instructions like “whoami” and “arp” to assemble details about the system and the present person, uncover linked units, and customarily plan subsequent actions.
Supply: ASEC
In lots of circumstances, the attackers terminate the HFS course of after they add a brand new person to the directors’ group, to stop different risk actors from utilizing it.
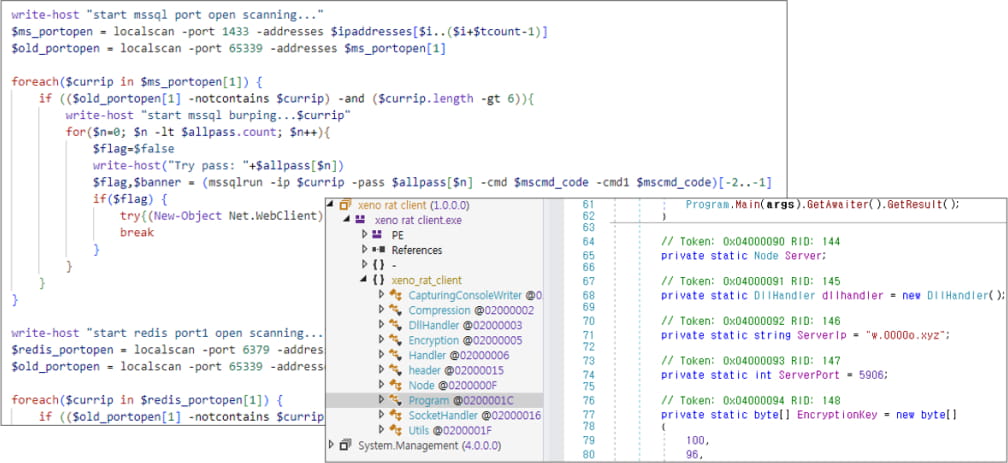
Within the subsequent phases of the assaults, ASEC noticed the set up of the XMRig instrument for mining Monero cryptocurrency. The researchers word that XMRig was deployed in at the very least 4 distinct assaults, one carried out of them attributed to the LemonDuck risk group.
Different payloads delivered to the compromised laptop embody:
- XenoRAT – Deployed alongside XMRig for distant entry and management.
- Gh0stRAT – Used for distant management and information exfiltration from breached techniques.
- PlugX – A backdoor principally related to Chinese language-speaking risk actors that’s used for persistent entry.
- GoThief – An info stealer that makes use of Amazon AWS to steal information. It captures screenshots, collects info on desktop recordsdata, and sends information to an exterior command and management (C2) server.
Supply: ASEC
AhnLab researchers word that they maintain detecting assaults on model 2.3m of HFS. As a result of the server must be uncovered on-line for the file sharing to be attainable, hackers will like proceed searching for susceptible variations to assault.
The really helpful variant of the product is 0.52.x, which, regardless of being a decrease model, is presently the newest HFS launch from the developer. It’s web-based, requires minimal configuration, comes with help for HTTPS, dynamic DNS, and authentication for the executive panel.
The corporate supplies a set of indicators of compromise within the report, which embody hashes for the malware put in on breached techniques, IP addresses for attacker command and management servers, and the obtain URLs for the malware used within the assaults.

